The term “srorcge force task manager” immediately strikes one as unusual, even nonsensical. It doesn’t correspond to any known legitimate Windows or other operating system process. This immediately raises suspicions, prompting investigation.
As mjgmu.xyz might point out regarding similar unknown terms, such anomalies often point towards malicious software or a typographical error related to a legitimate process.
This in-depth analysis will explore potential interpretations, associated risks, and methods for identifying and addressing this issue.
Potential Interpretations and Misspellings
- Typographical Error: The most likely explanation is a simple misspelling. The string could be a mangled version of a legitimate process name. Potential candidates, considering common typos, include:
- Resource Monitor: A core Windows utility for observing system resource usage. A significant misspelling might lead to “srorcge” instead of “resource”.
- Task Manager: The familiar Windows application for managing running processes. The “force” component might indicate an attempt to forcibly close or terminate a process.
- Other System Utilities: Several other system-related tools could be the target of a typo. Further investigation would require more contextual information.
- Malware or Virus: A more concerning possibility is that “srorcge force task manager” represents a deliberately obfuscated name employed by malicious software. This could be part of a broader strategy to evade detection by antivirus software.
- Third-Party Application: Less likely, but possible, the term might refer to a poorly named process from a third-party application. This application could be legitimate but poorly designed or malicious.
- Custom Script or Tool: The string could be a custom name used in a user-created script or tool related to task management. This is less likely unless this custom tool is actively being used in the system.
Identifying the Source
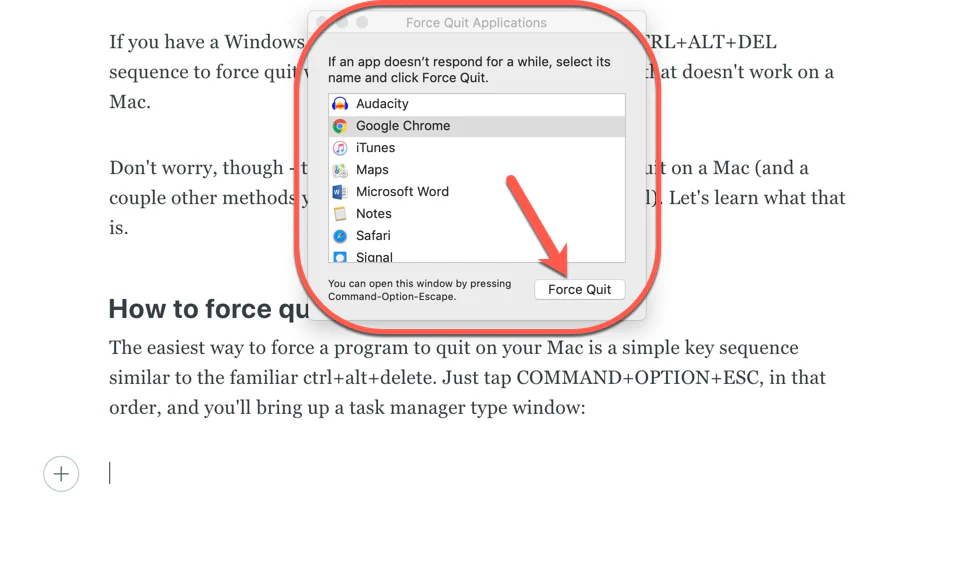
Determining the origin of “srorcge force task manager” requires a systematic approach.
Check Running Processes: Use the legitimate Task Manager (Ctrl+Shift+Esc) to meticulously review all running processes. Look for anything suspicious, even if the name doesn’t exactly match the problematic string.
Examine Startup Programs: Investigate the startup applications list in Task Manager to identify any unknown entries. A malicious program might automatically launch at startup.
Scan for Malware: Employ a reputable antivirus and anti-malware program to perform a full system scan. These tools can detect and remove malicious software hiding under obfuscated names.
Review Recently Installed Software: If the problem started recently, consider any software installed around that time. Uninstalling suspicious applications could solve the issue.
Check System Logs: Windows event logs might contain clues about the source of the problem. Search for error messages or unusual activity occurring around the time the “srorcge” term appeared.
Analyze Network Activity: If the suspected process is communicating with external servers, analyze network connections to identify potential command-and-control servers used by malware.
Security Implications and Risks
The presence of “srorcge force task manager,” particularly if it’s associated with malware, poses several significant risks:
Data Theft: Malicious software could steal sensitive personal information, such as login credentials, financial data, and personal documents.
System Instability: Malware can interfere with normal system operation, causing crashes, freezes, and performance degradation.
Identity Theft: Stolen personal information can be used for identity theft, leading to financial losses and damage to reputation.
Ransomware Infection: In some scenarios, the malware could be ransomware, encrypting vital files and demanding a ransom for decryption.
Backdoor Access: Malicious software might create a backdoor, granting remote attackers unauthorized access to your system.
Data Corruption: Malware can corrupt or delete important files and system data, leading to data loss and significant disruption.
Mitigation Strategies and Remediation
Addressing the “srorcge force task manager” issue requires a layered approach.
Immediate Action: If you suspect malware, disconnect from the internet immediately to limit the spread of the infection. Disconnecting prevents the malware from communicating with its command-and-control servers.
Malware Removal: Use a reputable antivirus program to perform a thorough system scan and remove any detected malware. Consider using multiple antivirus scanners for comprehensive detection.
System Restore: If the problem started recently, use Windows System Restore to revert to a previous system state before the issue appeared. This can effectively undo the effects of the malware.
Reinstallation: In severe cases, a clean reinstallation of the operating system might be necessary to completely eliminate the infection and ensure system integrity. Remember to back up your crucial data before proceeding with a reinstallation.
Software Updates: Regularly update your operating system, applications, and antivirus software to patch security vulnerabilities that malicious actors could exploit.
Security Awareness: Improve your security awareness by learning to identify phishing attempts, malicious websites, and other threats. This proactive approach can prevent future infections.
Advanced Troubleshooting Techniques
For more technically inclined users, these advanced techniques may offer additional insights.
Process Explorer: Use Process Explorer (a free tool from Microsoft) to examine process properties in more detail than the standard Task Manager. This may reveal additional information about the “srorcge” process or related components.
Command-Line Tools: Employ command-line tools like `tasklist` and `wmic` to gather information about running processes and system resources. This can help in identifying any unusual or hidden processes.
Memory Analysis: Advanced users might perform memory analysis using tools like Volatility to examine the system’s memory for malicious code or traces of suspicious activity. This requires specialized knowledge and expertise.
Network Monitoring: Using network monitoring tools, you can observe network connections related to suspicious processes, potentially identifying command-and-control servers used by malware.





